
Identifying security vulnerabilities in your code
Shift from reactive patching to proactive security. Find and fix vulnerabilities during development.

Shift from reactive patching to proactive security. Find and fix vulnerabilities during development.
Security vulnerabilities hide in plain sight within your production code despite extensive tooling. Your static analysis tools flag thousands of potential issues, creating noise that obscures genuine threats. Code reviews catch obvious flaws but miss edge cases that only surface when attackers systematically probe your authentication flows, input validation logic, and authorization checks.
Most security analysis happens reactively. You scan code after completing development, patch vulnerabilities after discovery, and harden systems after breaches.
This reactive approach demands deep security expertise to understand attack vectors, analyze complex codebases, and correlate vulnerability reports with actual business risk. The time between vulnerability introduction and detection creates windows where your production systems remain exposed to exploitation.
Here's how to shift from reactive security patching toward proactive vulnerability prevention.
You typically begin with automated Static Application Security Testing (SAST) tools that scan your entire codebase and generate vulnerability reports. These tools flag potential issues like SQL injection patterns, cross-site scripting (XSS) vulnerabilities, and insecure cryptographic implementations.
The challenge: they generate extensive alert volumes that require your manual triage to distinguish genuine security risks from false positives. You spend significant time validating whether flagged issues represent exploitable vulnerabilities or acceptable risks given your architectural constraints.
After automated scans, you perform manual code reviews focusing on critical paths like authentication flows, input validation, and authorization logic. You trace data movement through applications, identify privilege escalation vectors, and verify implementations follow security best practices.
Manual reviews catch sophisticated vulnerabilities that automated tools miss, such as logic flaws, business rule bypasses, and context-specific attack vectors. The challenge is scale: reviewing millions of lines across multiple services requires extensive time and security expertise that most teams lack.
Penetration testing involves hiring security professionals to simulate realistic attacks against your applications and infrastructure. These engagements test whether theoretical vulnerabilities discovered through automated scans and code reviews can actually be exploited by attackers.
Professional penetration testing provides realistic threat scenarios with clear business impact assessments. However, many companies conduct these tests quarterly or annually due to cost constraints and scheduling complexity.
This infrequent testing cadence leaves critical vulnerabilities undiscovered for extended periods. Additionally, penetration tests typically focus on currently deployed code, missing security issues introduced in your active development branches that won't reach production for weeks or months.
You can integrate AI coding assistants like Claude into your vulnerability analysis workflows. Analyze security patterns during active development, validate security implementations, and spot attack vectors that traditional scanners miss.
You can work with Claude in two different ways:
Claude.ai provides a free web interface where you can paste code snippets, describe your architectural patterns, and receive vulnerability assessments with specific remediation guidance.
Claude Code integrates directly into your development environment as an agentic terminal tool. It analyzes security patterns across your entire codebase, examines authentication flows spanning multiple services, and suggests security improvements directly within your development workflow.
Before investing time in comprehensive security reviews or scheduling penetration tests, you can quickly validate whether your coding patterns introduce vulnerabilities. This immediate feedback supports security-conscious decisions during development rather than discovering critical issues weeks later during QA or in production.
When security questions arise during development, paste small code snippets or describe architectural scenarios to get immediate analysis. Claude excels at explaining why certain approaches create vulnerabilities and suggesting secure alternatives that match your technology stack.
Common security questions you might ask:
This educational approach supports recognizing potential security issues during coding, making security considerations a natural part of your development process rather than an afterthought discovered during security audits.
Before implementing security controls, Claude can offer a fresh perspective on comprehensive threat models for new functionality. Describe your feature requirements and Claude identifies potential attack vectors, data exposure risks, and defensive strategies to consider during implementation.
Example: "We're building a file sharing feature where users can upload documents and share them with specific teams within our organization. What security considerations should guide the implementation?"
Claude outlines threats like path traversal attacks allowing unauthorized file access, malicious file uploads containing executable code, missing authorization checks enabling cross-team data access, and data exfiltration risks through unvalidated share links.
This comprehensive threat analysis provides you with security requirements early in development rather than discovering vulnerabilities during security testing phases.
Paste static analysis reports, penetration testing findings, or security scanner output into Claude. Ask for "vulnerability analysis ranked by exploitability and business impact."
Claude correlates technical findings with actual attack scenarios, explains why specific vulnerabilities matter, and provides targeted remediation steps. Instead of generic "fix SQL injection" recommendations, you get "parameterize the user search query in UserService.findByEmail() and validate email format before database calls."
When vulnerabilities span multiple services or require architectural changes, Claude Code provides project-wide vulnerability analysis that traditional security tools struggle to achieve.
Install:
npm install -g @anthropic-ai/claude-codeLaunch in your project:
claudeStart security analysis:
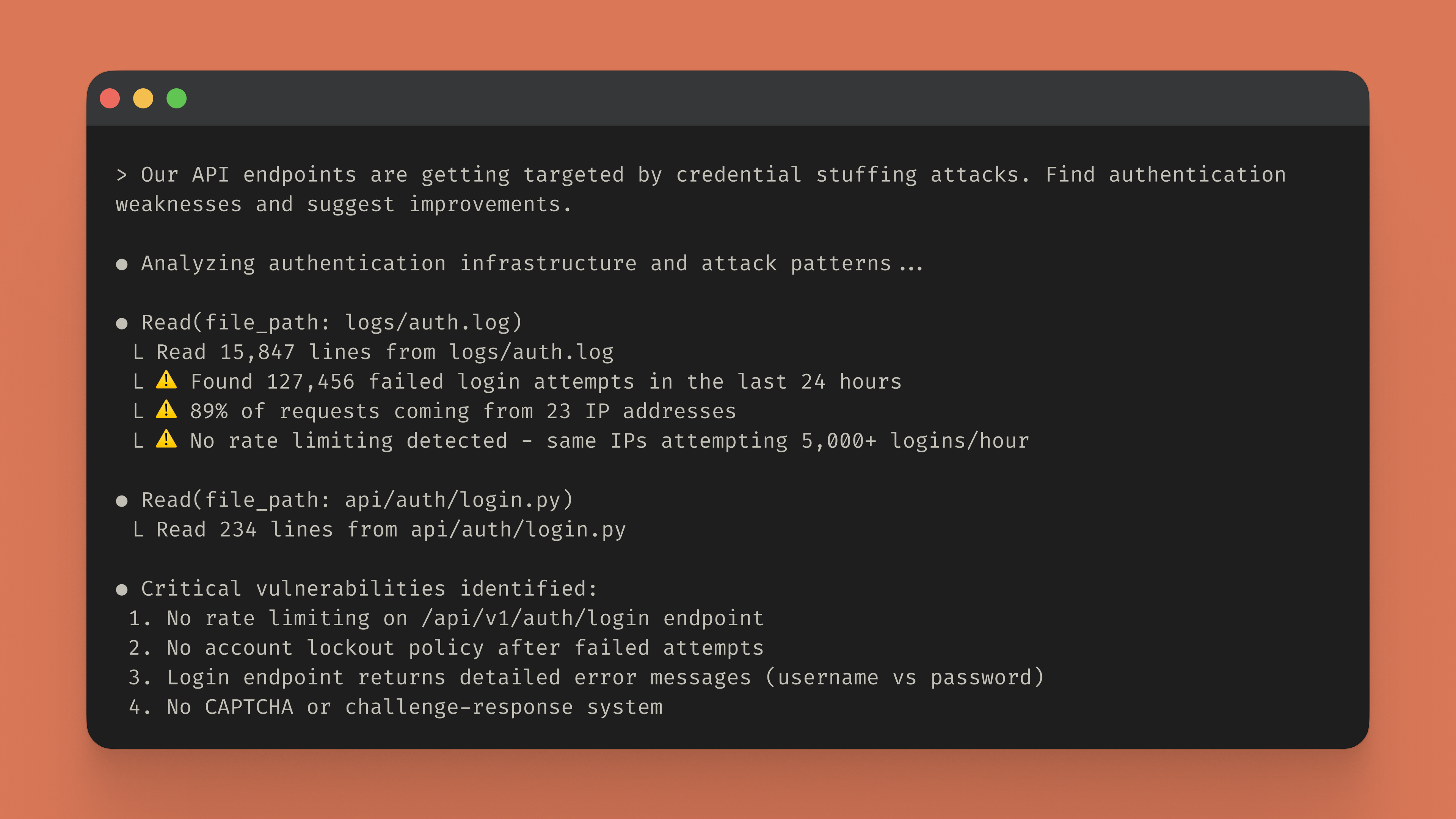
Claude Code autonomously analyzes authentication flows across your entire codebase, evaluates password policies, missing rate limiting, inadequate account lockout mechanisms, and suggests comprehensive hardening strategies.
Once Claude Code identifies vulnerabilities, it implements targeted fixes that integrate with your existing security architecture. Rather than applying generic security patterns, Claude Code analyzes your application context to suggest security improvements that work with your authentication systems, authorization models, and deployment constraints.
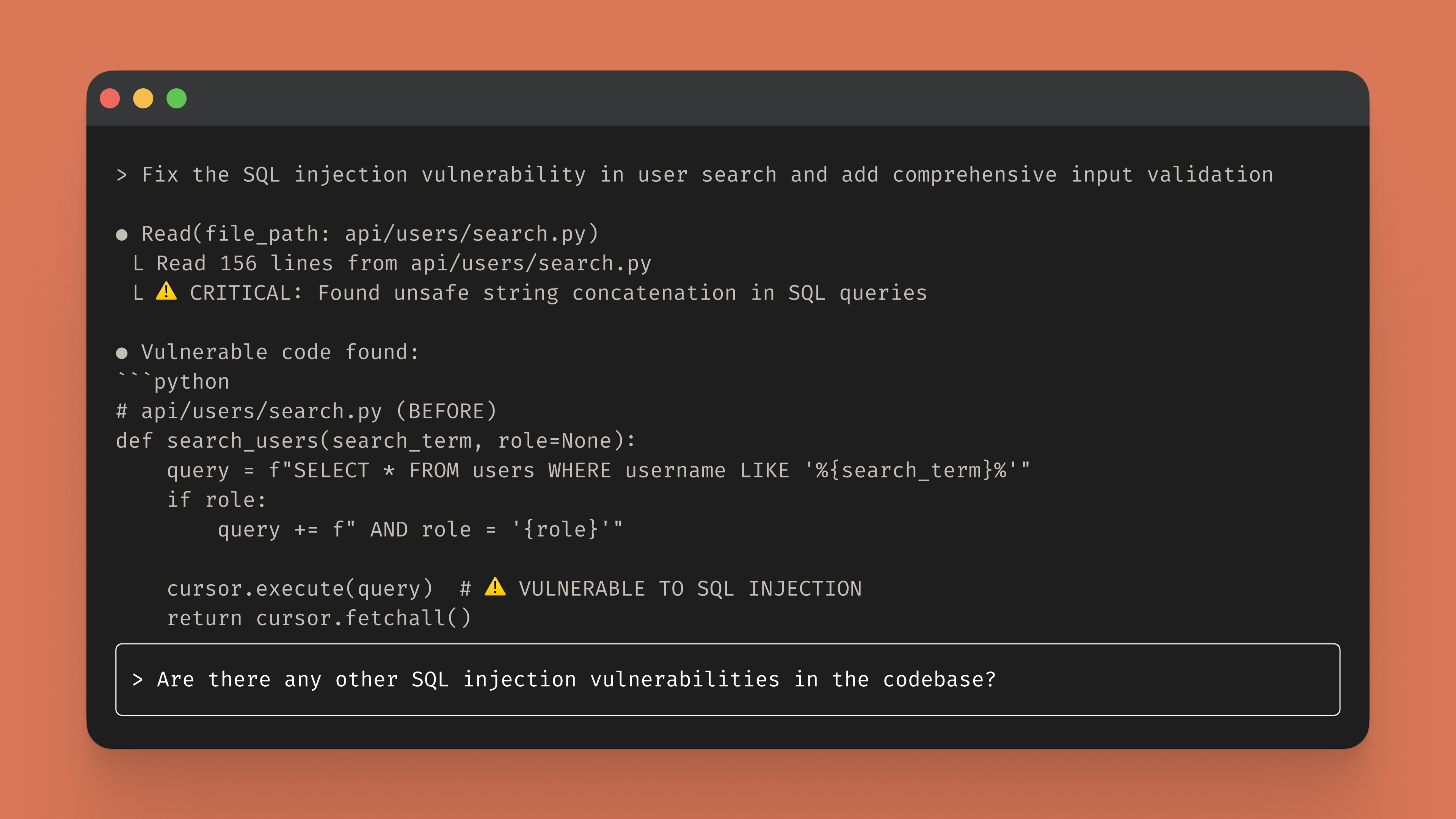
Claude Code implements parameterized queries to prevent SQL injection, adds input sanitization layers, integrates validation middleware, and generates security tests to verify the fixes work as intended.
The /security-review command analyzes your codebase for security vulnerabilities directly from your terminal. Run this command before committing changes to catch issues in your inner development loop, when fixes require minimal effort.
When you run /security-review, Claude Code systematically examines your code for common vulnerability patterns:
Claude Code identifies specific files and line numbers where vulnerabilities exist, explains the security risk in your application context, and suggests targeted fixes. After reviewing findings, ask Claude Code to implement remediation directly, keeping security corrections within your active development session.
This immediate feedback loop transforms security from a blocking gate at the end of development into continuous guidance during coding.
Claude.ai: Instant vulnerability analysis, threat modeling, and security architecture guidance. Ideal for analyzing code snippets, validating security approaches, and exploring attack scenarios before implementing features.
Claude Code: Project-wide security analysis, automated vulnerability remediation, and comprehensive security hardening. Run /security-review for ad-hoc terminal-based security checks before committing code. Designed for enterprise security workflows, establishing security standards across your codebase, and ensuring fixes integrate safely with your existing security architecture.
Start with Claude.ai to identify specific vulnerabilities and validate security approaches during development. Then, switch to Claude Code for system-wide security improvements and maintaining consistent security standards across your entire development environment.
npm install -g @anthropic-ai/claude-codeWhether you're preventing injection attacks, implementing secure authentication, or hardening API endpoints, Claude helps identify vulnerabilities and suggest remediation strategies, reducing time spent on manual security analysis while ensuring no code ships without security validation.



Get the developer newsletter
Product updates, how-tos, community spotlights, and more. Delivered monthly to your inbox.